In today’s interconnected world, both homes and small businesses rely on secure network infrastructures to safe- guard their operations, personal information, and valuable data. Cybersecurity threats continue to evolve, making it more crucial than ever to ensure your network is secure and resilient against potential vulnerabilities. Our Network Vulnerability Assessment Services are designed to help you identify and mitigate risks, providing peace of mind and protecting you from cyber-attacks.
Our team of experts uses cutting-edge tools and industry-standard techniques to assess the security posture of your network. By performing a comprehensive vulnerability assessment, we help you discover weak points in your system before cybercriminals can exploit them. We provide tailored recommendations to enhance your security, ensuring your network remains safe from threats.
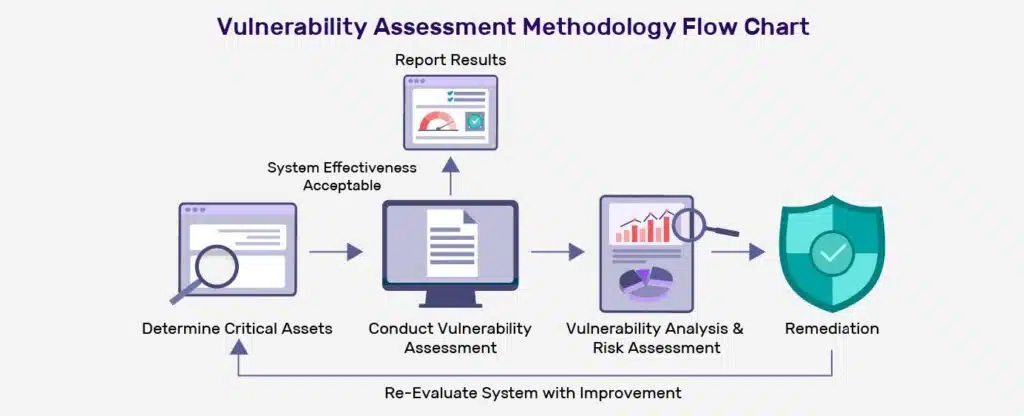
We follow a thorough and systematic approach to ensure that no stone is left unturned in your network security assessment:
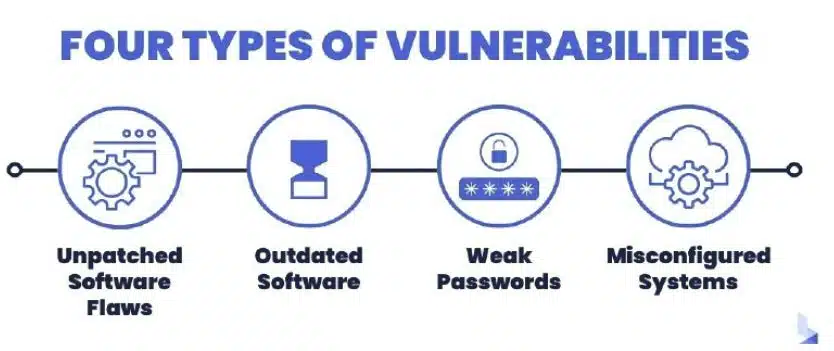
Here are some of the most common network vulnerabilities that we address during our assessments:
Our Home and Small Business Network Vulnerability Assessment services are offered through a strategic partnership between Prudential Associates and K17 Security, combining our strengths and expertise to offer a seamless, comprehensive solution. By leveraging the specialized capabilities of both firms, we ensure that clients receive best- in-class service, enhanced innovation, and exceptional value.
With cyber threats growing daily, it’s imperative to stay ahead of attackers. Protect your network with our comprehensive vulnerability assessment services. Don’t wait until it’s too late. Contact us today and take the first step toward securing your home or business